Introduction
The increasing complexity of Kubernetes environments presents unique security challenges, particularly regarding lateral movement attacks. Honeypots offer a strategic advantage in detecting and preventing these threats by acting as decoy systems that appear legitimate to attackers but are actually isolated and heavily monitored.
Kubernetes environments are particularly vulnerable to lateral movement due to their distributed nature, complex networking, and the potential for compromised pods, service accounts, or nodes to serve as entry points for further exploitation.
The diagram illustrates a typical lateral movement scenario in a Kubernetes environment:
- Initial Access: an attacker compromises an initial pod (possibly through a vulnerable application);
- Privilege Escalation: from within the compromised pod, the attacker accesses the automatically mounted Service Account token;
- API Enumeration: using the token, the attacker queries the API Server to discover available resources in the cluster;
- Resource Discovery: the attacker identifies Secrets and ConfigMaps that might contain sensitive information;
- Secrets ex-filtration: the attacker gains access to credentials stored in Secrets;
- Use of stolen credentials: with the stolen credentials, the attacker can access databases or other external services;
- Cross-pod access: the attacker moves laterally to other more critical pods;
- Access to critical resources: from the last compromised pod, the attacker can access internal systems of the organization;
- Data ex-filtration: the culmination of the attack consists of exfiltrating sensitive data.
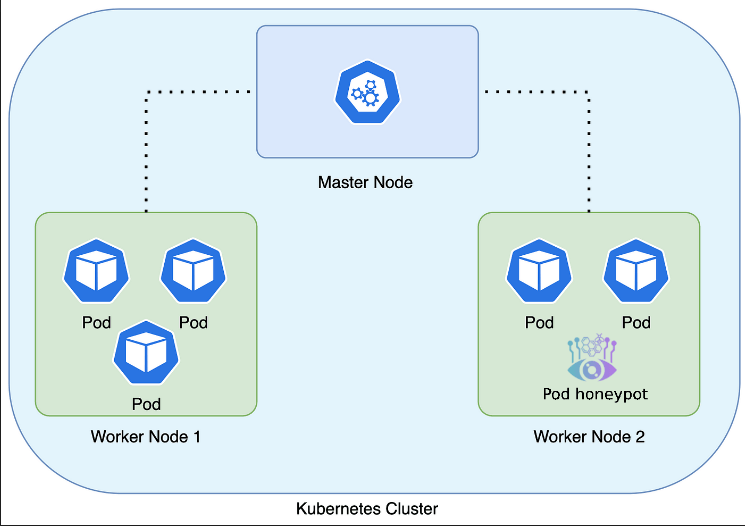
For this reason, deploying honeypots in Kubernetes environments can be an effective strategy to detect and prevent lateral movement attacks.

If you want to learn more about Kubernetes lateral movements, I recommend the video: Lateral Movements in Kubernetes, Yossi Weizman
Configure and deploy Beelzebub on kubernetes
Pre requirements:
- kubectl installed and context configured https://kubernetes.io/docs/tasks/tools/install-kubectl/
- helm installed https://helm.sh/docs/intro/quickstart/
Below are the commands to download, configure and deploy beelzebub.
- Clone Beelzebub repository:
$ git clone https://github.com/mariocandela/beelzebub.git
- You can rewrite the chart default values with a
custom-values.yaml
Follow example of custom-values.yaml
image:
repository: m4r10/beelzebub
pullPolicy: IfNotPresent
tag: v3.0.0
beelsebubServiceConfigs: |
apiVersion: "v1"
protocol: "ssh"
address: ":2222"
description: "SSH interactive"
commands:
- regex: "^ls$"
handler: "Documents Images Desktop Downloads .m2 .kube .ssh .docker"
- regex: "^pwd$"
handler: "/home/"
- regex: "^uname -m$"
handler: "x86_64"
- regex: "^docker ps$"
handler: "CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES"
- regex: "^docker .*$"
handler: "Error response from daemon: dial unix docker.raw.sock: connect: connection refused"
- regex: "^uname$"
handler: "Linux"
- regex: "^ps$"
handler: " PID TTY TIME CMD\n21642 ttys000 0:00.07 /bin/dockerd"
- regex: "^(.+)$"
handler: "command not found"
serverVersion: "OpenSSH"
serverName: "ubuntu"
passwordRegex: "^(root|qwerty|Smoker666|123456|jenkins|minecraft|sinus|alex|postgres|Ly123456)$"
deadlineTimeoutSeconds: 60
service:
type: ClusterIP
port: 2222
- Deploy:
Defaults values:
$ helm install beelzebub ./beelzebub-chart
Custom values
$ helm install beelzebub ./beelzebub-chart -f custom-values.yaml
Regarding alert and monitoring, you can use the Prometheus and Grafana stack, or fluentd to send logs to a SIEM.
Conclusion
Deploying honeypots in Kubernetes environments can be an effective strategy to detect and prevent lateral movement attacks. Beelzebub is a honeypot framework, you can configure it to mimic the kubernetes core component like kube-apiserver, kube-controller-manager, kube-scheduler, kubelet, kube-proxy.
The Beelzebub team is dedicated to making the internet a better and safer place ❤️