Mario: You can’t defend. You can’t prevent. The only thing you can do is detect and respond. By Bruce Schneier
Overview
As cybercrime continues to be a major threat to businesses and individuals, it’s important to have effective measures in place to detect attacks.
One such measure is the use of a honeypot, a computer system that is set up to attract and trap cybercriminals or malware in order to study their behavior.
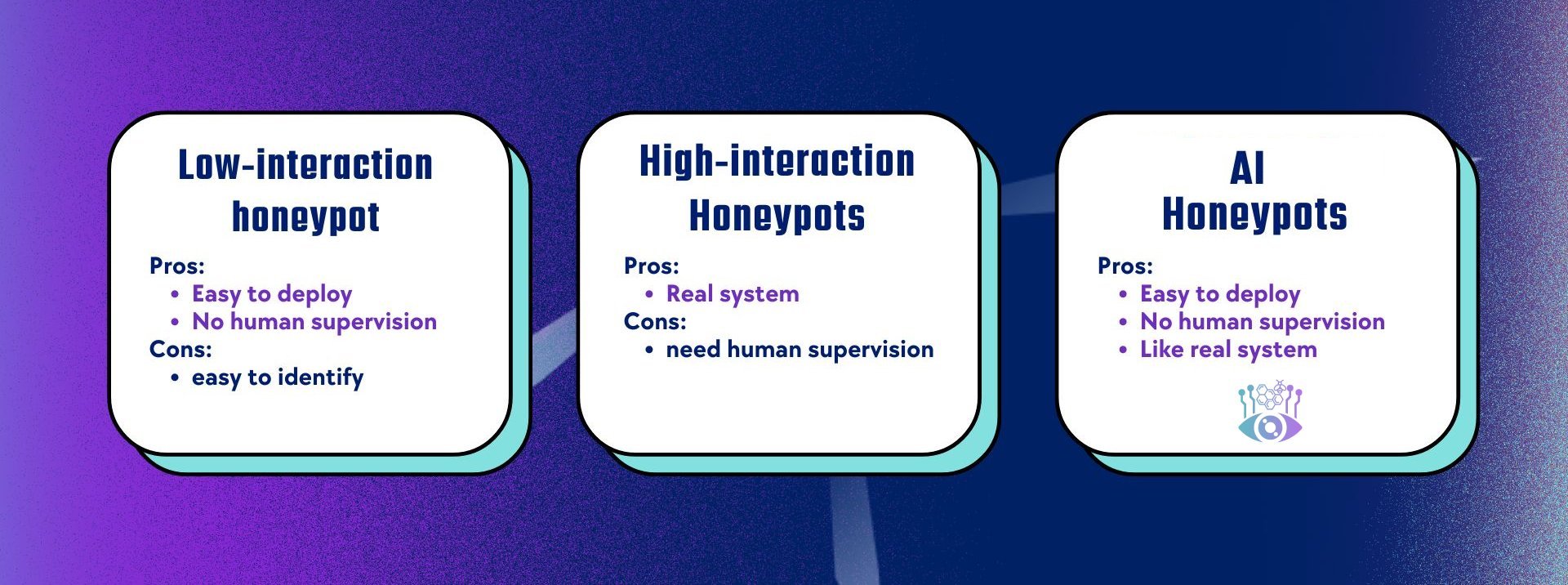
Traditionally, we have two types of honeypots. Low-interaction honeypots rely on static data and rules, making them easily detectable by cybercriminals or malware. Another solution is high-interaction honeypots, which are fully functional computer systems but require constant supervision.
That’s where LLM Honeypot comes in. You don’t have to supervise it, and it replicates a real environment.
LLM honeypot implemented with Beelzebub framework:
The following lines illustrate how to implement an AI honeypot using the Beelzebub framework.
apiVersion: "v1"
protocol: "ssh"
address: ":2222"
description: "SSH interactive LLM honeypot"
commands:
- regex: "^(.+)$"
plugin: "LLMHoneypot"
serverVersion: "OpenSSH"
serverName: "ubuntu"
passwordRegex: "^(root|qwerty|Smoker666|123456|jenkins|minecraft|sinus|alex|postgres|Ly123456)$"
deadlineTimeoutSeconds: 60
plugin:
llmModel: "llama3"
host: "http://example.com/api/chat" #default http://localhost:11434/api/chat
apiVersion: "v1"
protocol: "http"
address: ":8080"
description: "HTTP honeypot LLM
commands:
- regex: "^(.+)$"
plugin: "LLMHoneypot"
statusCode: 200
plugin:
llmModel: "gpt4-o"
openAISecretKey: "sk-proj-123456"
For more information, please visit our Docs